 The latest Skybox Vulnerability and Threat Trends Report is now out, and it presents some eye-opening statistics and trends that security analysts at Skybox Research Lab have been tracking over the past year. For anyone interested in the on-the-ground realities confronting security professionals these days, the report makes for compelling reading.
The latest Skybox Vulnerability and Threat Trends Report is now out, and it presents some eye-opening statistics and trends that security analysts at Skybox Research Lab have been tracking over the past year. For anyone interested in the on-the-ground realities confronting security professionals these days, the report makes for compelling reading.
Get the 2022 report here
This year’s findings chart a threat landscape that’s expanding and diversifying at a blistering clip. We observed record growth in new vulnerabilities affecting a wide variety of products. In particular, vulnerabilities in operational technology (OT) skyrocketed, nearly doubling versus the previous year. As vulnerabilities emerged, threat actors moved ever more quickly to weaponise them. New exploits increasingly took aim at the latest vulnerabilities, while malware producers nimbly tuned their product mix to capitalise on cybercrime hotspots such as cryptojacking and ransomware. Let’s take a closer look at our key findings:
Vulnerabilities have more than tripled over the past 10 years
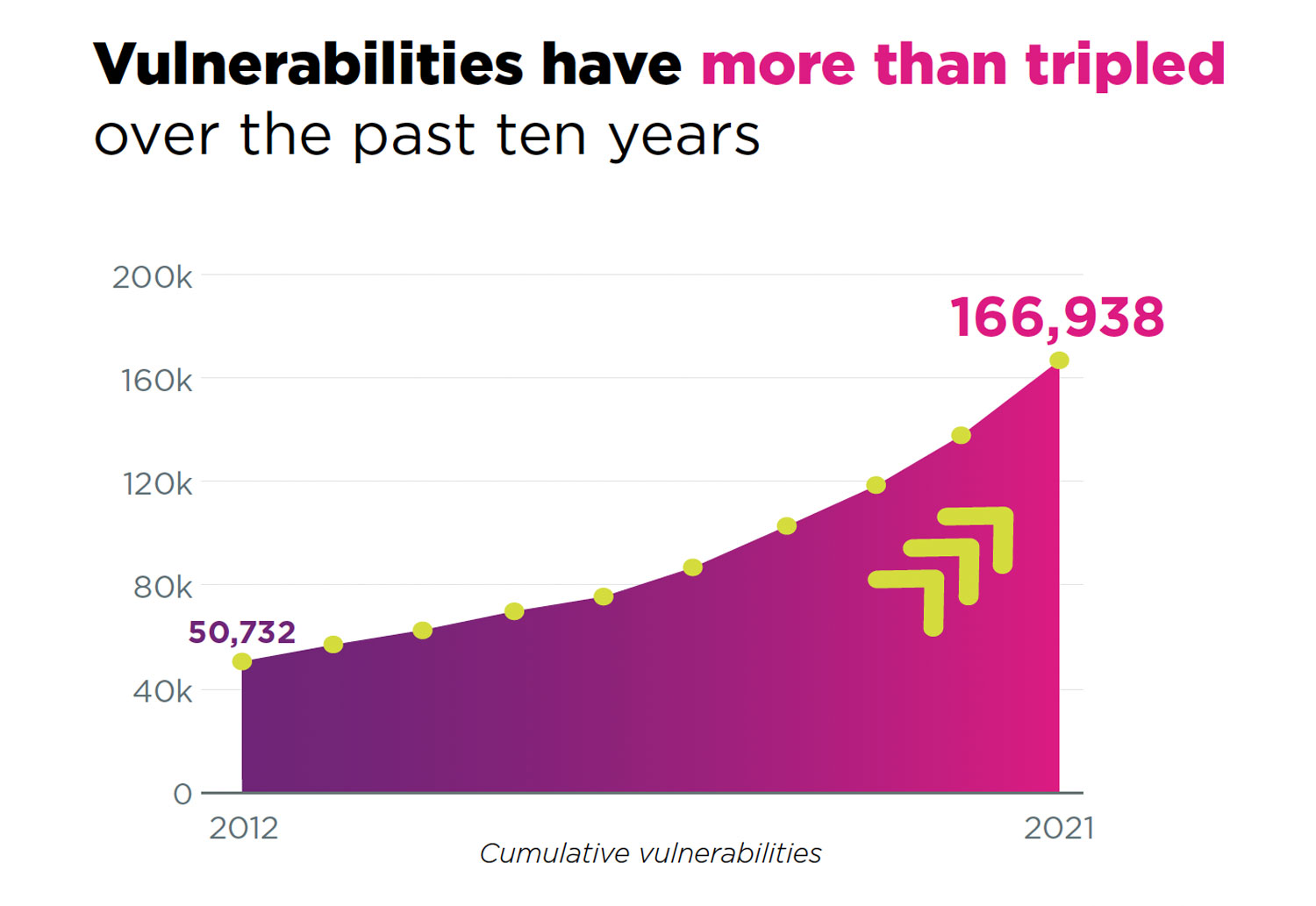
New vulnerabilities smashed records, hitting an all-time high in 2021, with 20 175 new CVE (common vulnerabilities and exposures). That’s up 10% from 2020 — the biggest percentage jump we’ve seen since 2018 and the first time new vulnerabilities have topped 20 000 for a single year.
This latest crop of vulnerabilities adds to a mountain of accumulated security debt. The total number of CVEs published over the last 10 years reached 166 938 in 2021 — a three-fold increase over a decade.
OT vulnerabilities nearly double in one year
As rapid as the rise in overall vulnerabilities was, security flaws in OT products grew even faster, increasing by 88% year over year. These vulnerabilities are especially worrying given the precarious state of OT security. The number of OT devices deployed in enterprises has risen dramatically in recent years. Many of these systems have few or no cybersecurity controls in place and are increasingly connected to networks, exposing them to attacks. Learn how Skybox “scan less” vulnerability detection helps you find “unscannable” OT vulnerabilities.
Cryptojacking and ransomware top new malware charts
Malware producers are turning out a widening array of products and services keyed to the latest cybercrime trends. The number of new cryptojacking and ransomware programs grew by 75% and 42% respectively, reflecting a growing demand for these increasingly lucrative and popular forms of exploit. Easy-to-use malware, exploit kits and malware-as-a-service (MaaS) have made it remarkably simple for non-expert hackers to mount attacks and reap rapid financial returns.
Faster weaponisation of vulnerabilities
One of the more notable trends we identified is the shrinking interval between the appearance of vulnerabilities and the development of exploits designed to take advantage of them. We found 168 vulnerabilities that were published in 2021 and targeted by exploits within the same year. That’s 24% more than the number of vulnerabilities published and subsequently targeted by exploits in 2020. It’s another sign that threat actors are upping their game and moving more aggressively to cash in on emerging opportunities.
Among those newly discovered vulnerabilities that were promptly exploited is the notorious Log4Shell vulnerability — a flaw in the massively popular Log4j open-source library that’s used in hundreds of millions of devices. The Log4Shell vulnerability was publicly disclosed in early December 2021. By the end of the month, there were already known 15 malware programs designed to exploit it.
As vulnerabilities mount, attacks follow
These trends leave security teams between a rock and a hard place. Proliferating vulnerabilities are creating more opportunities for breaches, and new malware and exploits are making it easier than ever for bad actors to capitalise on those opportunities.
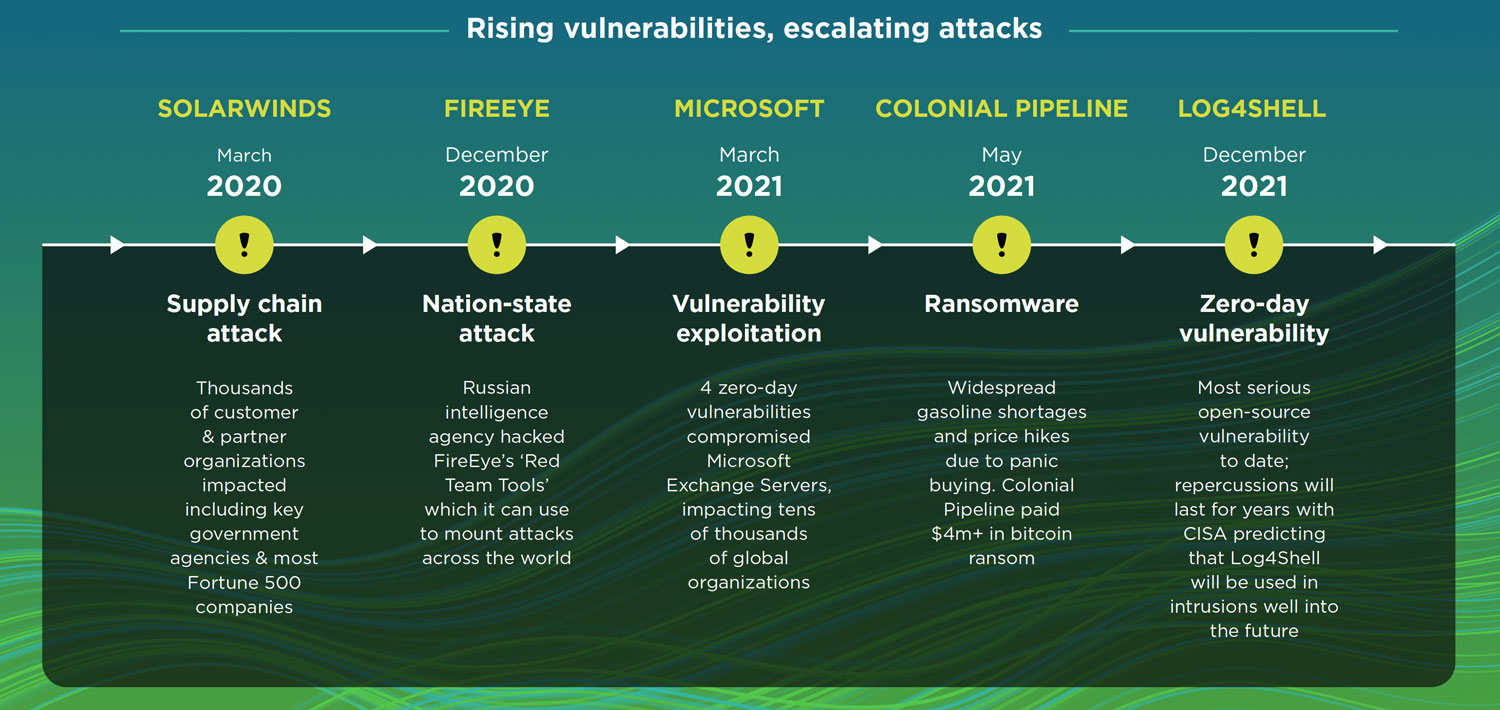
It’s a worst-of-both-worlds combination, emboldening threat actors and leading to more frequent and more audacious cyberattacks. In 2021 we witnessed some of the most brazen incidents to date:
- Zero-day attacks more than doubled in 20211. A series of zero-day attacks exploited vulnerabilities in Microsoft Exchange Server, impacting tens of thousands of organisations.
- Supply-chain attacks, such as those targeting IT software from SolarWinds and Kaseya, as well as the Log4Shell vulnerability.
- Critical infrastructure attacks, wreaking havoc on vital operations and services. Examples include the Colonial Pipeline ransomware attack that disrupted fuel supplies in the south-eastern US.
The average cost of data breaches hit $4.24-million, up nearly 10% from 20202
Clearly the old vulnerability management playbook that many organisations still rely on is badly out of step with today’s threat landscape. Traditional, reactive measures such as scanning and patching are too little, too late in a world where the attack surface is exploding, vulnerabilities are rampant (and are often difficult or impossible to scan and patch), and threat actors are increasingly aggressive. It’s time to get out of reactive mode and embrace a truly proactive security posture.
In future instalments of this series, we’ll dive deeper into the report’s findings and discuss what they mean for the future of vulnerability management. Subscribe to our blog to catch the latest.
Learn more about the Skybox Research Lab.
References
- 2021 has broken the record for zero-day hacking attacks, Technology Review, MIT, September 23, 2021.
- 2021 Cost of a Data Breach Report, IBM, July 28, 2021.
- This promoted content was paid for by the party concerned

